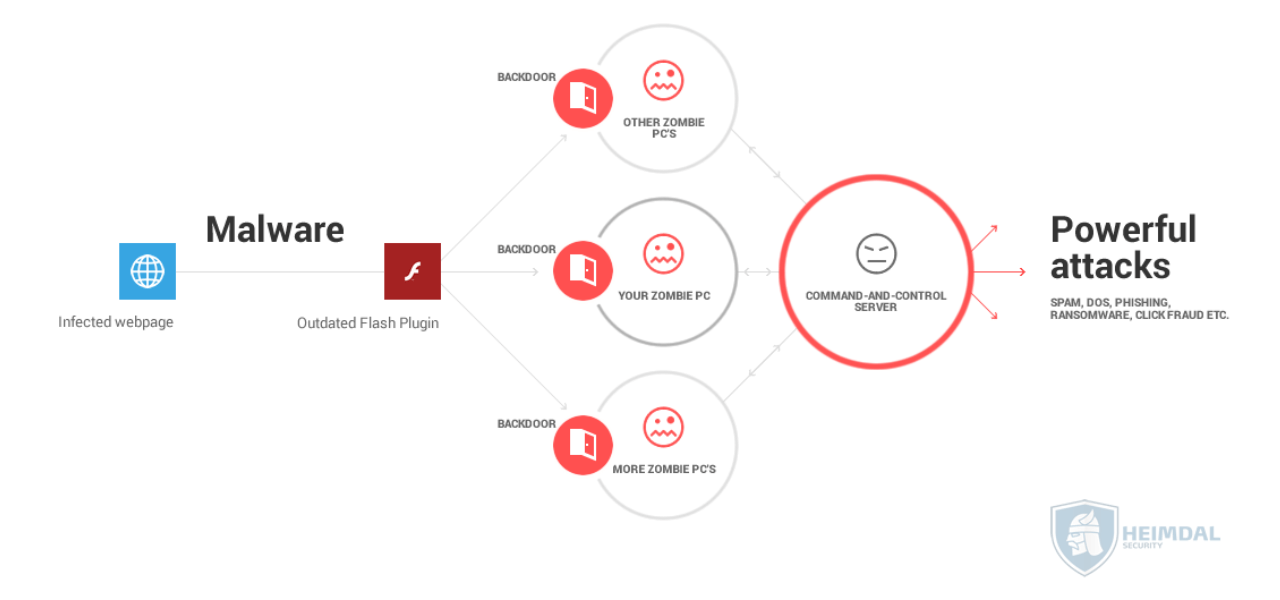
Product Item: Trojan attack online
What is a Trojan Virus Trojan Horse Malware Imperva online, What is a Trojan Horse Virus Types Prevention in 2024 online, What Is a Trojan a Virus or Malware How Does It Work Avast online, What are Banking Trojans GeeksforGeeks online, How trojan malware is evolving to survive and evade cybersecurity online, What is Proxy Trojan GeeksforGeeks online, Trojan Attacks How Does Trojan Horse Infect Devices online, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus online, Trojan attack PPT online, What is a Trojan Horse Virus Types Prevention in 2024 online, Trojan Malware Understanding the Rising Threat of Cybercrime online, Scheme of a Trojan horse attacks with different wavelengths from online, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet online, Trojan horse attacks threaten the security of practical quantum online, What is a Trojan horse attack Shiksha Online online, What are Trojan Viruses and How Do These Threats Work Top Cloud online, What is a Trojan Horse Virus Types and How to Remove it online, Threat Actors Target Government of Belarus Using CMSTAR Trojan online, Trojan Horse Meaning Examples Prevention online, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses online, What Are Trojans How Can You Protect Yourself online, Cybercrime horse internet trojan virus Business Flow Chart online, Trojan attack PPT online, What is a Trojan Horse U.S. News online, What is a Trojan Horse What does the Trojan Virus do online, Threat Actors Target Government of Belarus Using CMSTAR Trojan online, How to Tell if Your Computer Is Infected by a Trojan Horse online, What Is a Trojan Virus Definition Prevention Removal Tips online, Hybrid Trojan Bio Cyber Hacking Attack. Steps 1 3 indicate a online, What Is a Trojan Virus Definition Prevention Removal Tips online, Trojan Virus Vector Symbol With Laptop And Red Trojan Horse Stock online, What s the Difference Between Malware Trojan Virus and Worm online, Trojan horse virus mal ware cyber security attack Vector Image online, How the attacker used the Trojan horse to attack Download online, What are Trojan Viruses and How Do These Threats Work Top Cloud online.
Trojan attack online